Islamic State West Africa Province (Iswap) could be close to using delivery drones for attacks in the Lake Chad Basin. Weaponising and adapting unmanned aerial vehicles (UAVs) is a new trend in the group’s operational strategy, and could worsen the conflict.
Institute for Security Studies (ISS) research shows that Iswap is already trialling delivery drones to carry improvised explosive devices. This includes assessing the weight that can be carried, how far they can go and how long they stay in the air. The threat goes beyond military targets and may impact humanitarian service delivery.
Ongoing operations by Nigeria’s military and clashes with Boko Haram faction, Jama’atu Ahlis-Sunna Lidda’Awati Wal-Jihad (JAS), have inflicted heavy losses on Iswap and significantly reduced its space to operate. And successful intelligence-driven strikes resulting in arrests of Iswap members outside the north-east are preventing the group from expanding. These setbacks may be forcing Iswap to adapt its strategy, as it has done before.
So far, Iswap’s use of drones has been limited to propaganda, surveillance and communication. ISS research, including analysis of publicly available propaganda materials and interviews with former combatants and associates, reveals an elaborate use of communication technology (see Chart 1). This includes satellite and android phones, drones, social media (Telegram and WhatsApp), high-speed printers, laptops, high-definition digital cameras, Wi-Fi, clip-on microphones, walkie-talkies, and data compression and archiving software.
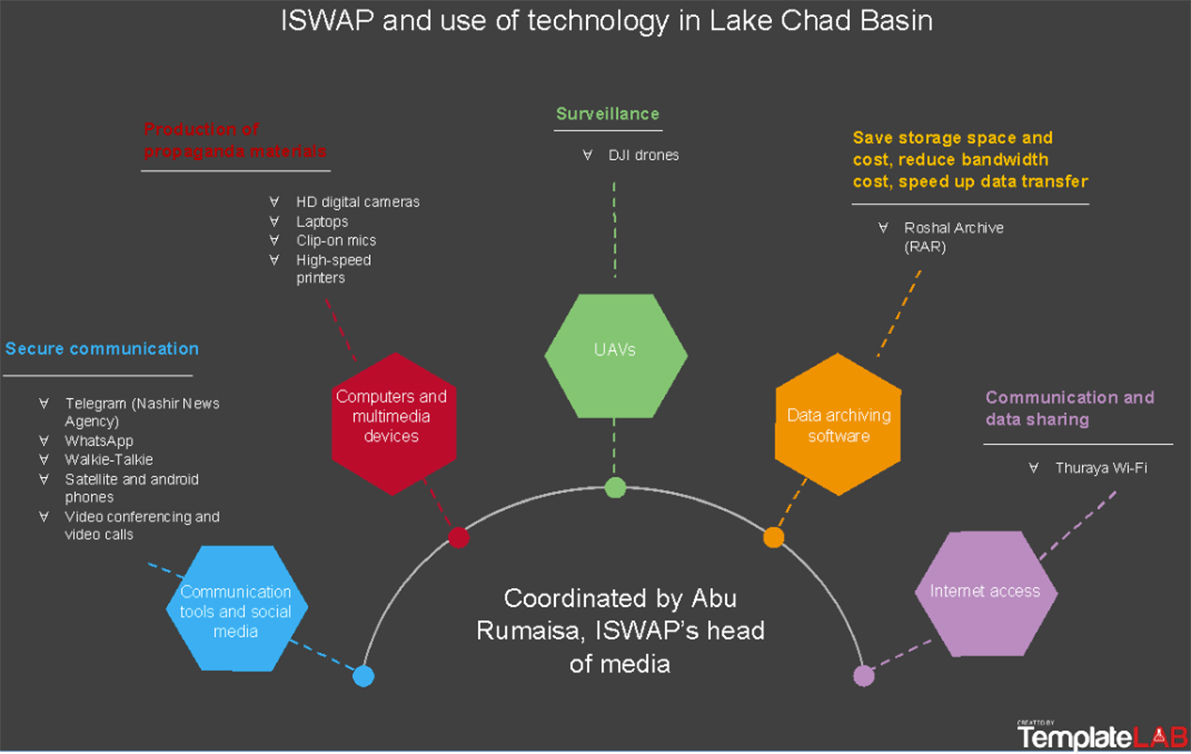 Chart 1: Use of technology by Iswap. (Graphic: Supplied by ISS Today)
Chart 1: Use of technology by Iswap. (Graphic: Supplied by ISS Today)
All these tools are used by the media team headed by Abba Yusuf (Abu Rumaisa), son of late Boko Haram founder Mohammed Yusuf. The team’s primary function is to showcase Iswap as a successful jihadist group. That propaganda will encourage recruitment and present a positive image that cements its position as the top Islamic State affiliate globally. The media department also handles relations with other violent extremist groups, including Islamic State.
Former Iswap members, including from the media unit, told ISS how the department functions. Staff are recruited from within the group and taught the basics of operating the equipment, mostly cameras. They accompany fighters and wait at a distance to be invited to take photos and videos, usually when things go Iswap’s way.
The raw footage and pictures are sent to Islamic State, which produces the propaganda material. The group shares the content with Iswap’s media team, which distributes it through a private and members-only Telegram account, Nashir News Agency (see Chart 2).
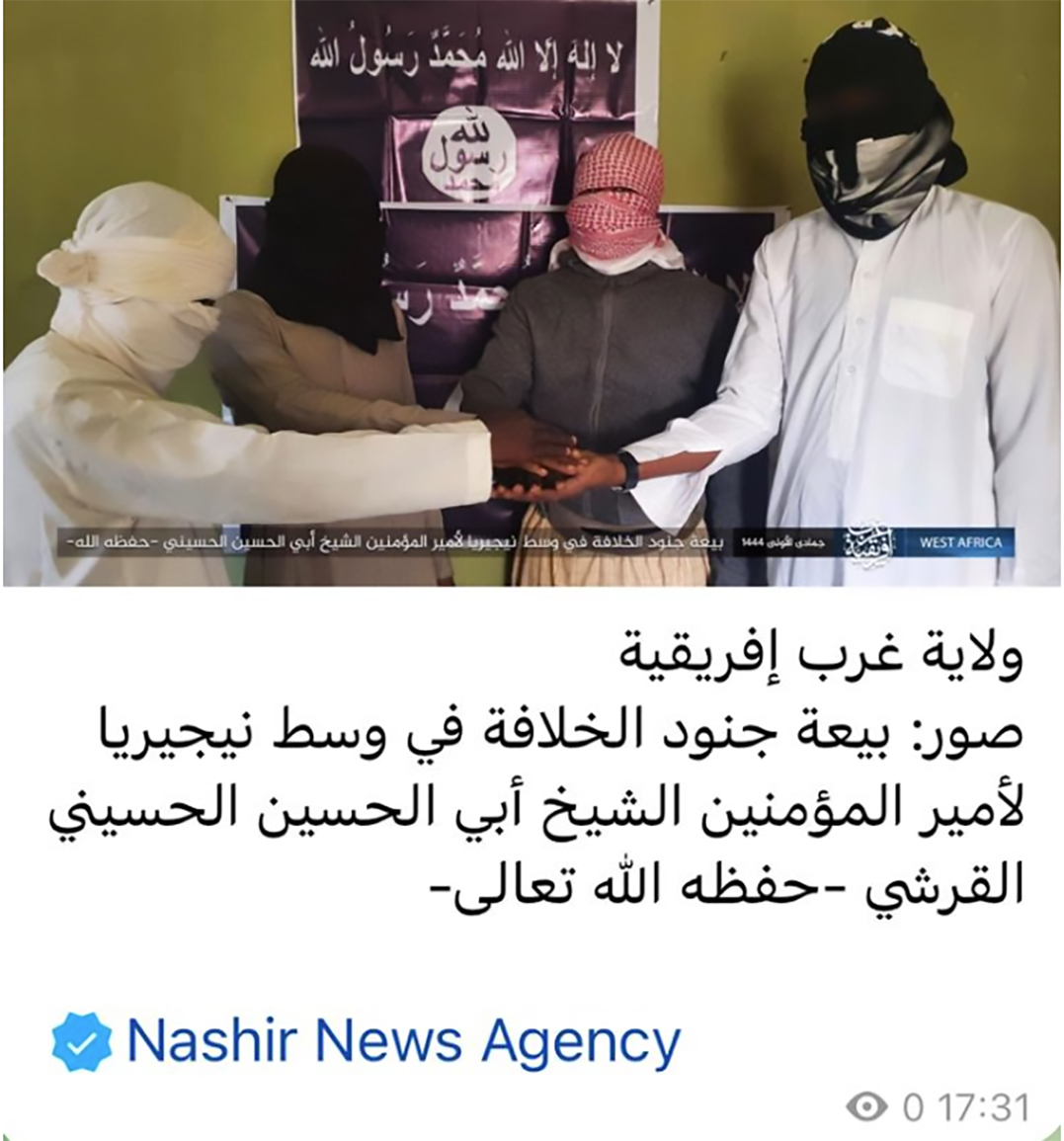 Chart 2: Propaganda image released in 2022 on Telegram, showing IS pledge of allegiance in Northwest Nigeria (Supplied by ISS Today)
Chart 2: Propaganda image released in 2022 on Telegram, showing IS pledge of allegiance in Northwest Nigeria (Supplied by ISS Today)
Iswap relies heavily on high-speed satellite internet to communicate with Islamic State and other groups. Sources told ISS that Iswap used Thuraya Wi-Fi and spent about $6,000 monthly on data. They said Lagos was the main supply source but that Iswap encountered a problem with the supply, forcing it to switch to Chad. Although Thuraya satellite phones and internet services are illegal in Chad, they are used in secret.
A particular Thuraya model stands out as a possible device used by Iswap. It is available in Nigeria but mainly in Lagos. The Thuraya XT-Hotspot is marketed as the “world’s fastest Wi-Fi via satellite for communication needs beyond GSM coverage … for quick and secure Internet connectivity in the remotest of locations.”
The sources claim Iswap has dedicated vehicles fitted with internet services to facilitate communication and data sharing on the go. The media team uses one of these vehicles when it accompanies fighters, enabling them to immediately share material from the battlefield. This explains how Iswap can release information quickly, including images and videos, sometimes within hours of attacks.
Iswap’s public communication also suggests it can easily share data with Islamic State using data compression and archiving software. In addition to speed and encryption, the software reduces bandwidth costs.
There is no single way to deal with the problem of Iswap’s use of technology. The solution lies in various measures working together.
ISS research has detailed how Iswap exploited Lake Chad Basin trade routes to get vital supplies. The group’s remote location should be an advantage for security forces who could disrupt its supply lines. Checkpoint searches have proved successful and can be used again. Those bringing in equipment and accessories should explain their destinations, which security agents should verify. Collaboration among security forces in the four affected Lake Chad Basin countries can help.
The ISS report also showed how civilian and military collaborators helped Iswap get supplies. Security force leaders in the region must hold their personnel to the highest standards and use an independent ombudsman to deter corruption. To prevent civilians from collaborating with terror groups, authorities should work with communities and trade unions to identify and disrupt networks helping Iswap. The criminal justice system can also play a deterrent role.
A future concern is that violent extremist groups like Iswap become involved in cybercrime. Given Nigeria’s enormous financial powers and growing tech industry, authorities should prepare for this. Investing in technology and collaborating with tech companies to prevent their products, platforms or services from falling into Iswap’s hands is a start.
Going after Iswap’s money is vital. The group should be forced out of its current location using targeted and joint military operations. This would cut Iswap’s access to its major revenue base. In using these tactics, care should be taken to avoid adversely affecting civilians, either by destroying their livelihoods or inflicting human rights violations.
Curtailing Iswap’s access to technology will prevent it from using tech to plan and execute attacks, spread propaganda and recruit. That will reduce the damage the group inflicts on civilians and aid workers in the Lake Chad Basin. DM
Malik Samuel, Researcher, Institute for Security Studies (ISS) Regional Office for West Africa, the Sahel and the Lake Chad Basin.
Research for this article was funded by the Government of The Netherlands.
First published by ISS Today.




