On 3 October the International Consortium of Investigative Journalists released the ‘Pandora Papers’ — a treasure trove of documents exposing attempts by wealthy elites to hide their assets and cash in offshore tax havens.
Thirty-five current and former heads of state were named after 2.9 terabytes of leaked data that were processed, picked over, packaged and published by a global team of hundreds of journalists. It’s a potent reminder of the power of data and its ability to expose illicit cash flows and dubious business deals that deprive the fiscus of much-needed tax revenues.
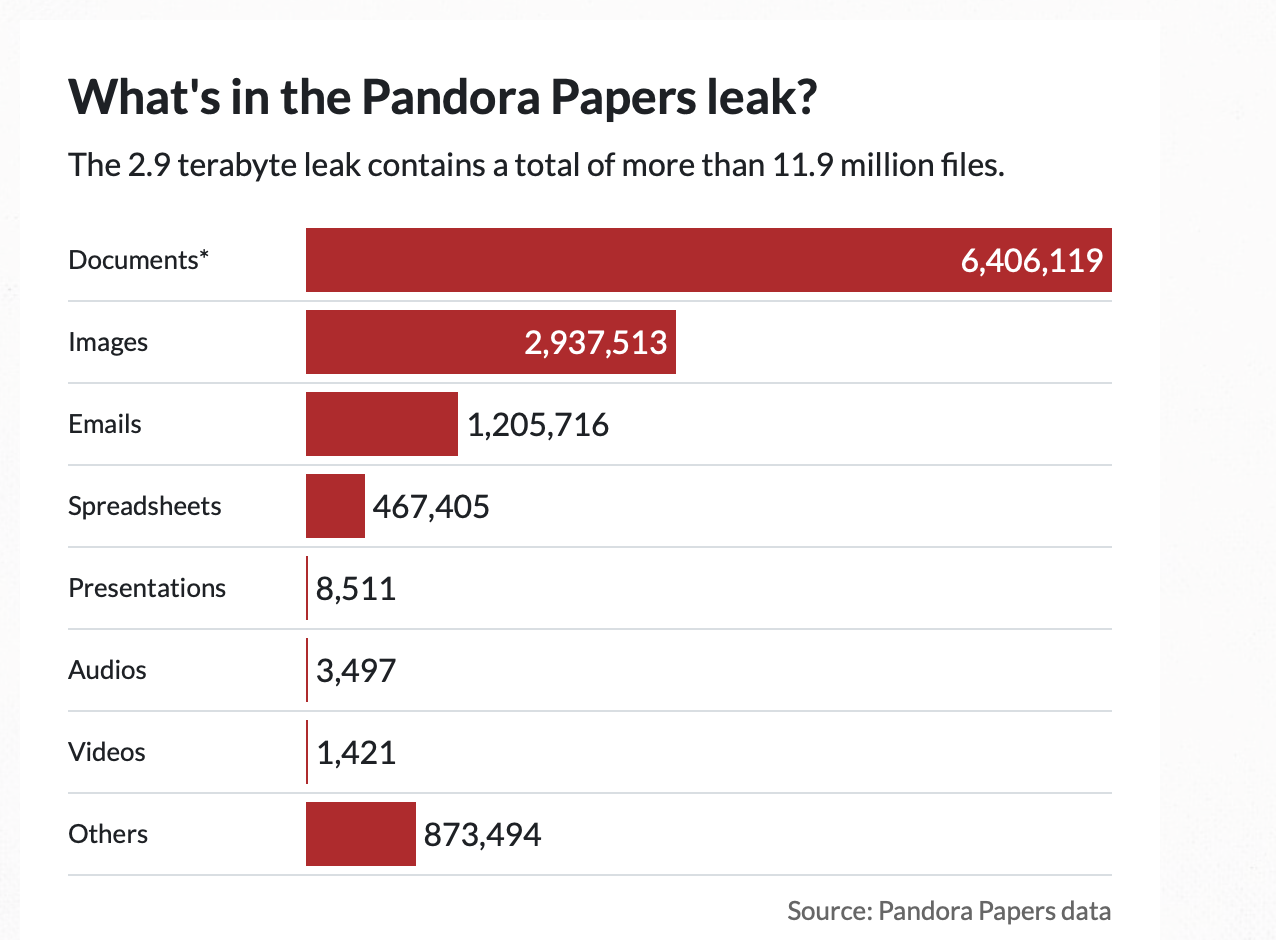 Breakdown of the contents of the 2.9 terabyte Pandora Papers leak. (Graph: Supplied by ISS Today)
Breakdown of the contents of the 2.9 terabyte Pandora Papers leak. (Graph: Supplied by ISS Today)
In Africa, where many of the pillars of democracy remain fragile, including a free media, the use of data to force accountability is one of the transformative properties of emerging tech. While caution is needed in an era of fake news and deliberate mis/disinformation campaigns, the power of data to achieve greater accountability of those elected or appointed to serve the public cannot be underestimated.
The Pandora Papers and its 2016 predecessor, the Panama Papers, were based on leaked data. But the development of investigative databases to hold public bodies such as municipal authorities or police departments to account, and open-source investigation tools (OSINT), make it easier for investigators to follow the electronic clues.
This is what the experts often call the ‘digital exhaust’ that follows our every interaction online. Machine learning and powerful algorithms have enabled huge troves of data to be organised methodically and processed at speed in a way that wasn’t previously possible. The data can be packaged and contextualised in a timely manner that demands action.
It is important to distinguish between leaked data such as the Pandora and Panama Papers, and open-source data, which anyone can access on the internet through OSINT tools. These include applications such as Google Dork, which allow search operators to identify specific details of a person/company or other entity buried in websites.
In contrast, leaked data isn’t always made public. Some may be redacted by journalists or non-governmental organisations (NGOs) before the details are released into the public domain. They are essentially ‘gatekeepers’, and one of their key functions is to give the leaked material context.
Having leaked data in the public domain is essential because it also gives law enforcement access to investigate illicit flows, corruption, and other financial crimes. This is an ethical issue insofar as journalists and NGOs consider themselves as conveyors of information, but not cyber sleuths or intelligence operatives acting on behalf of the state.
Civil society organisations in South Africa are using open-source data tools to encourage citizens to hold government agencies to account. “While we haven’t the skills and resources to use forensic technology,” argues David Lewis, Executive Director of Corruption Watch, “we are using contemporary tech to assist us on the ground.”
At the beginning of 2021, Corruption Watch launched the Veza Tool to make the police service more accountable. Veza, which means to ‘expose’ or ‘reveal’ in isiZulu, aims to combat corruption and “break the cycle of impunity in the police service.” The app enables citizens to access details of police resources, locations and personnel across the country using heat maps. They can then compare these with lived experiences.
Lewis sees enormous potential in developing data tools to force more responsibility in South Africa. “We are trying to build up a best practice on procurement, but if the country had a database that listed every single contract, it would make accountability so much easier.” ISS Today understands research is underway to develop a tool that would match the allocation of South African government tenders against a database of government officials, to expose patronage networks.
The World Bank recently hosted a symposium on using data tools to detect and measure corruption and assess the effectiveness of policies designed to combat it. Among the analytics being run largely in Europe — which could be replicated in Africa with sufficient funding support — are European Public Accountability Mechanisms. These examine political financing and public procurement. Another, Opentender, analyses tender data mainly from European jurisdictions.
Using open-source research techniques by organisations such as Bellingcat has enabled researchers to access free online tools. These include programmes or applications to track shipping and aircraft movements and geolocating individuals or objects such as military hardware. It also provides reverse engineering technology for verification and accessing phone and email databases.
Bellingcat’s methodologies are frequently made public, and their findings have exposed alleged human rights abuses in Africa, including in Cameroon and Burundi, which become a catalyst for legal investigations. They’ve also been used to uncover information campaigns regarding the notorious Gupta family in South Africa and shed light on Russia’s shadowy Wagner Group’s operations in Africa.
Access to alternative data is a powerful bulwark against attempts to erode the democratic space, especially when newspapers are silenced and social media sites switched off in numerous African countries. Arguably, the monopoly of information enjoyed by many states for years is rapidly being eroded.
For those African governments committed to consolidating their democracies, this is an opportunity for state prosecutors, investigators and other government officials to arm themselves with new data tools. They should embrace the power of big data to facilitate accountability and efficiency, tackle criminality and improve service delivery, thereby setting a standard for other African states to follow.
African policymakers and their partners should consider working with academic institutions and the private sector to develop similar databases to the accountability tools being rolled out across Europe. These would arm citizens with information to confront transgressions and offer investigators leads to gather further evidence to mount prosecutions. DM
Karen Allen, Consultant, ISS Pretoria.
First published by ISS Today.




 Breakdown of the contents of the 2.9 terabyte Pandora Papers leak. (Graph: Supplied by ISS Today)
Breakdown of the contents of the 2.9 terabyte Pandora Papers leak. (Graph: Supplied by ISS Today)