With its total revenue for 2018 at around R107-billion, China’s Hangzhou Hikvision Digital Technology currently leads the global video surveillance industry. Incorporated in 2001, Hikvision established a South African branch in 2015, and last year they opened a new office in Johannesburg.
But the partnership with Vumacam will see Hikvision’s footprint in South Africa grow substantially, and Vumacam also hopes to establish surveillance networks throughout Cape Town in the future.
Vumacam’s system uses Hikvision’s IP cameras; each camera has a unique IP (internet protocol) address that identifies it on the Internet and allows it to “communicate” with other devices (just like any computer, modem, or smart TV connected to the net).
A residents’ association can rent Vumacam’s surveillance services for R730 a month per camera. Vumacam owns the cameras, stores the footage and controls access to all data. Security companies contracted by residents to monitor camera feeds can only view the footage of that specific neighbourhood.
 Hikvision: Soon 15,000 high definition Hikvision IP cameras will be watching Johannesburg’s suburbs. (Image supplied)
Hikvision: Soon 15,000 high definition Hikvision IP cameras will be watching Johannesburg’s suburbs. (Image supplied)
It’s meant to curb crime, but since 2013 researchers have discovered several cybersecurity vulnerabilities in Hikvision’s products – most of which required very little skill to be exploited by hackers. Cyber vulnerability is a weak spot (an error in the code) of a computer program that a hacker can use to get into your computer, smartphone, IP camera, etc and wreak all sorts of havoc. The program or code that hackers design to get through that weak spot is called an exploit. An exploit can allow a hacker to remotely control a device, infect it with malware, or access data.
 A snapshot from a Vumacam online advertisement: The company plans to roll out thousands of high-definition surveillance cameras to curb crime throughout Joburg’s suburbs this year, and hopes to eventually expand its networks to other parts of the country.
A snapshot from a Vumacam online advertisement: The company plans to roll out thousands of high-definition surveillance cameras to curb crime throughout Joburg’s suburbs this year, and hopes to eventually expand its networks to other parts of the country.
Annually, cybersecurity researchers discover thousands of vulnerabilities in software and firmware. (Roughly put, the firmware is software that comes built into the hardware. Without it, the device is useless. Other software, like Mac OS or Windows, runs “on top of” firmware, if you will. It’s often in the firmware of Hikvision’s surveillance equipment that vulnerabilities have been discovered.) Simultaneously, hackers design exploits, and although not every vulnerability is penetrated, no manufacturer is immune to attacks. The security organisation Risk Based Security reported that over 22,000 vulnerabilities were discovered in 2018.
Once a vulnerability is discovered, the manufacturer usually fixes it with a tweaked program called an update, patch, or fix. The onus is on the manufacturer to act fast in supplying the fix. It’s the camera owner’s job to install the update as soon as possible.
But in the past, Hikvision has taken its time.
In 2013, the research company Core Security discovered three vulnerabilities in the firmware of one Hikvision model, the DS-2CD7153-E Network Mini Dome Camera. The company suspected that as many as 165 other Hikvision camera models using the same firmware were affected, but this remains unconfirmed.
The vulnerabilities were remotely exploitable, meaning that the hacker could launch the attack over the Internet, from anywhere in the world. Between the three weak spots, they allowed a hacker to access all camera data, render the camera useless, or send commands to control it. One vulnerability was one of the most serious ever known to be discovered in a Hikvision product.
As serious as it gets.
Not all cyber vulnerabilities are equal. Some are easier to exploit than others. Some will allow a hacker to take complete control of a device and even use it to do serious damage to other Internet services. Others may simply allow a hacker to render a device useless, or only allow partial access to the device’s data.
This is where the Common Vulnerability Scoring System (CVSS) comes into the picture. It’s an international industry standard, and basically a scale of zero to 10. A score of one means the vulnerability does not pose a big threat. A score of 10 means it’s very easy to design an exploit and will lead to serious damage. With so many cyber vulnerabilities out there, cyber security teams have to deal with the most serious ones first. The CVSS is aimed at helping them prioritise.
One of Hikvision’s 2013 vulnerabilities scored a perfect 10.
 The Hikvision DS-2CD7153-E Network Mini Dome Camera may be ‘vandal proof’, but the same could not be said for its immunity to cyber vandals. Its 2013 vulnerability was assigned the most serious security rating possible. (Image supplied)
The Hikvision DS-2CD7153-E Network Mini Dome Camera may be ‘vandal proof’, but the same could not be said for its immunity to cyber vandals. Its 2013 vulnerability was assigned the most serious security rating possible. (Image supplied)
Core Security contacted Hikvision four times over three weeks to warn them. After a month passed with no response, the researchers posted details of the vulnerabilities on the Core Security website and warned the public not to expose their cameras to the Internet “unless absolutely necessary”.
Similar incidents of unresponsiveness from Hikvision followed.
In 2014, cybersecurity company Rapid7 discovered three vulnerabilities in certain Hikvision digital video recorders, or DVRs. DVRs are connected to the cameras, and they record what is filmed.
The vulnerabilities made it possible for a hacker anywhere in the world to access the DVRs. Two of these vulnerabilities enabled hackers to slow down or even shut down the DVR. The third vulnerability allowed hackers to take full control of it.
Rapid7 said their research revealed many manufacturers with vulnerable products, but the “Hikvision models in particular” were “very popular...with around 150,000 devices remotely accessible”.
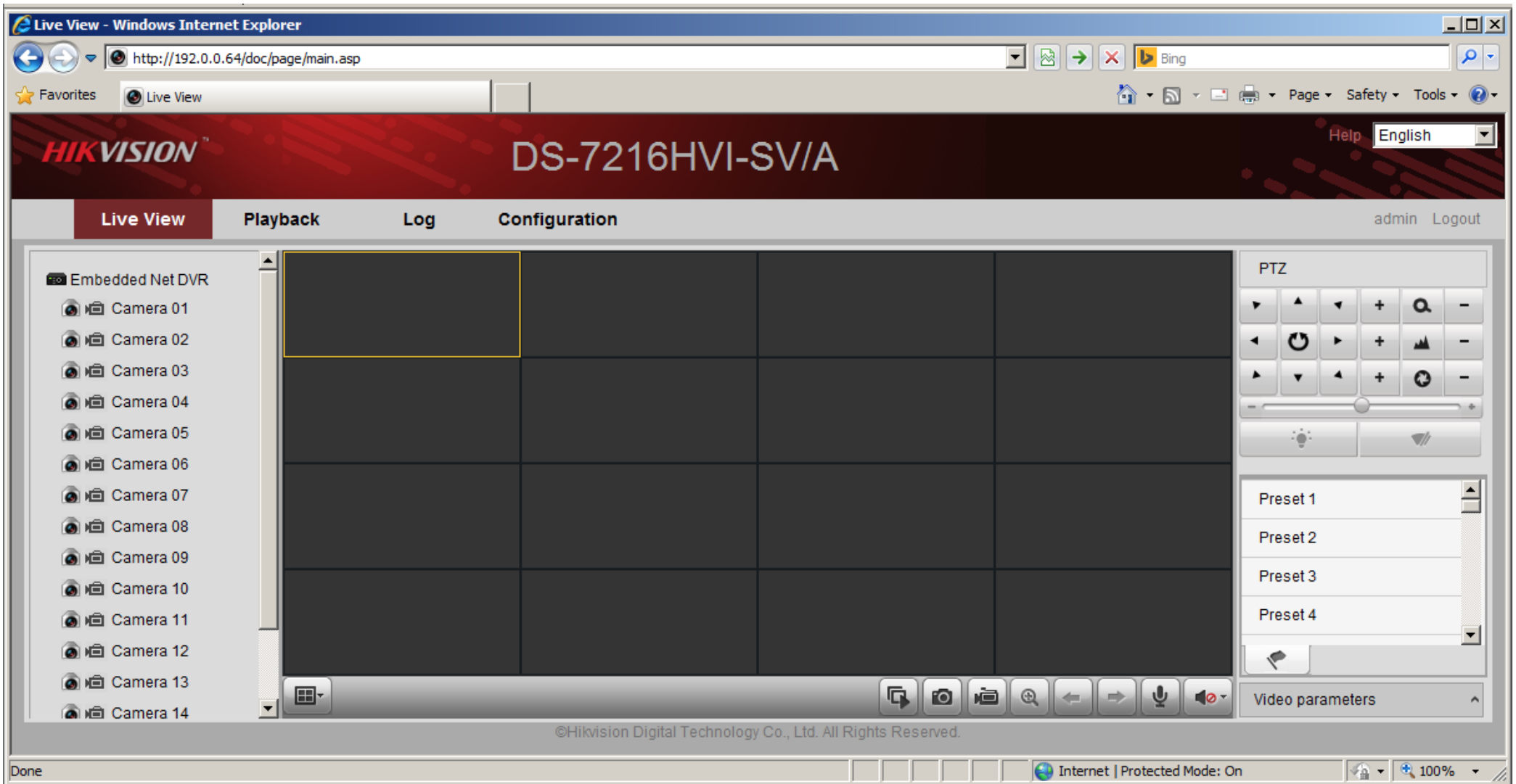 A user interface for a Hikvision digital video recorder (DVR). You need a username and password to log in and operate the DVR, but in 2014 cyber security experts at the Rapid7 research company reported that the Hikvision DVR model DS7204 and other models in the same series could be completely taken over by a hacker. (Source: Rapid7)
A user interface for a Hikvision digital video recorder (DVR). You need a username and password to log in and operate the DVR, but in 2014 cyber security experts at the Rapid7 research company reported that the Hikvision DVR model DS7204 and other models in the same series could be completely taken over by a hacker. (Source: Rapid7)
According to Rapid7, “Hikvision provided no response to these issues after several attempts to contact them.” Thus, on 19 November 2014, more than two months after their first warning to Hikvision, Rapid7 disclosed the problem to the public, advising consumers that “Hikvision DVR devices and similar products should not be exposed to the internet without the usual additional protective measures”.
Then in 2016, independent researcher Iraklis Mathiopoulos discovered how to hack Hikvision’s global cloud servers. The vulnerability would allow an attacker to get hold of private customer data stored on the server from a remote location.
More specifically, Mathiopoulos was investigating one of Hikvision’s cloud cameras. As the name suggests, this type of camera is connected to a Hikvision cloud storage facility, also known as a cloud server. You access the camera through these cloud servers. Whatever the camera films is uploaded to the server. After this, you have to log into the server to look at your videos. This allows you to see what’s going on at your house through an app on your smartphone.
Mathiopoulos said that “ultimately, it wouldn’t be that difficult to get access to more than 100,000 cloud-based cameras and DVRs (digital video recorders). The vulnerable servers are part of the backend system of hik-online.com, a service that Hikvision offers to access your PVRs (personal video recorder) and cameras via the web.”
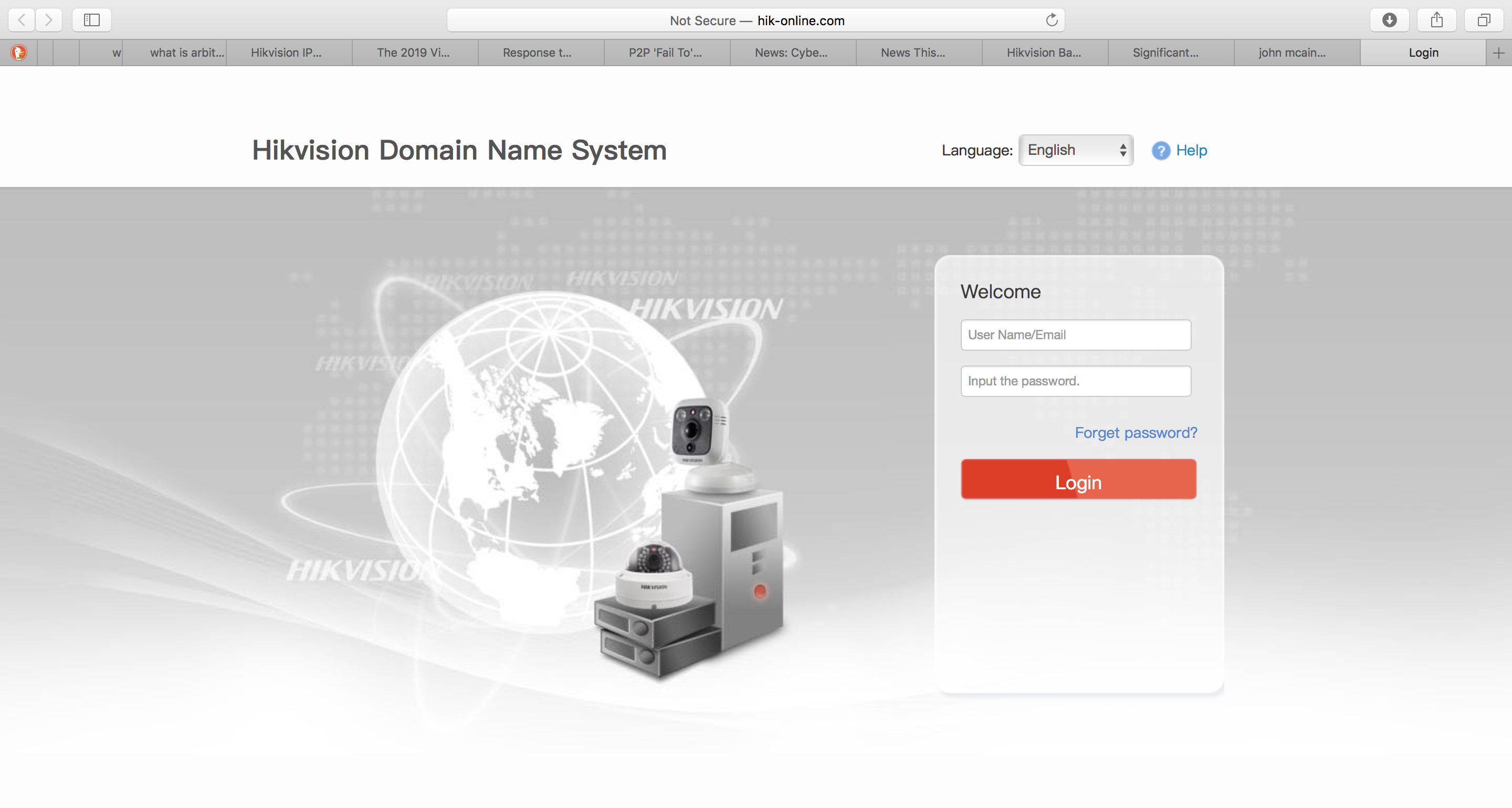 A landing page for hik-online.com. Researcher Iraklis Mathiopoulos discovered a vulnerability in Hikvision’s cloud servers, a service that gives camera users access to their IP cameras and video recorders via the Internet. This is the login page for the cloud servers, but Mathiopoulos found a way around the username and password.
A landing page for hik-online.com. Researcher Iraklis Mathiopoulos discovered a vulnerability in Hikvision’s cloud servers, a service that gives camera users access to their IP cameras and video recorders via the Internet. This is the login page for the cloud servers, but Mathiopoulos found a way around the username and password.
Mathiopoulus said that he alerted Hikvision to the problem on 25 August 2016. It took nearly two weeks and three emails from Mathiopoulus before they responded. On 8 September 2016, Hikvision let him know that they had fixed the problem, and asked him to try to hack in again. As a reward for helping them solve the problem, Hikvision sent him a camera valued at $69.
These incidents reveal that it hasn’t been uncommon for outside companies and individuals to discover Hikvision product vulnerabilities, despite Hikvision having a dedicated in-house Cyber Security Centre.
For an indication of why this is the case, Daily Maverick spoke to cyber security expert John Honovich. Honovich heads IPVM, a group of independent experts that test IP-based surveillance products from all over the world. We asked Honovich if he believed that the state of affairs was a reflection on the inadequacy of Hikvision’s cybersecurity research efforts.
Honowich’s answer: “That's hard to tell, because sources close to the company tell us that when Hikvision discovers vulnerabilities (or their contracted security people do) in existing production products, they will fix it but not let the public know. Our understanding is that Hikvision does this to limit negative media coverage, but it puts users at risk who assume the existing firmware does not have issues.”
The implication of this is that there could be many more vulnerabilities than Hikvision lets on, and many more vulnerable products.
Fortunately, in the above incidents, no devices were actually hacked. But that’s not always been the case.
In February 2015 the Chinese government itself became a victim of a cyber attack. Hikvision equipment within the surveillance system of China’s Jiangsu province was hacked. The Jiangsu Provincial Public Security Department saw it as a serious threat and ordered “all local public security science and technology information offices to carry out a comprehensive inventory of all Hikvision equipment” and to establish stronger passwords and eradicate viruses. This is according to a Hikvision press statement, which this time was released almost immediately after the hack was discovered.
 In February 2015, hackers from outside China hacked IP cameras at the facilities of the Jiangsu Provincial Public Security Department. (Source: Google Maps)
In February 2015, hackers from outside China hacked IP cameras at the facilities of the Jiangsu Provincial Public Security Department. (Source: Google Maps)
Hackers had reportedly exploited weak usernames and passwords (like admin and 12345). These were the original factory default settings that remained unchanged when the cameras were first installed. Not changing default passwords and usernames of any computer application can lead to significant security issues, because the passwords are easy to guess.
But the Jiangsu hack could also have been prevented with measures taken by the manufacturer. For instance, manufacturers can programme their software to prompt – or force – the customer to create a new username and password upon first switching on the device.
Weak default passwords weren’t news to Hikvision.
In April 2014, there was another Hikvision hacking incident involving weak passwords. A researcher at the Sans Technology Institute discovered malware that had infected Hikvision’s digital video recorders. The aim: To turn the processors inside the recorders into Bitcoin miners. As the name suggests, Bitcoin miners are computer processors used to generate the online currency, Bitcoin.
A high-powered processor far stronger than that of a video recorder is needed to effectively mine Bitcoin. But the hackers infected the devices regardless and, as the tech website Wired noted in their report on the issue, this hack was probably a “side-effect” of the rapidly growing Internet-of-Things (IoT). With all manner of devices joining the internet, ranging from IP cameras to fridges, microwaves, medical equipment and baby monitors, hackers have new targets. At the end of 2018, there were an estimated seven billion IoT devices (not including phones, laptops and tablets) connected online.
And if you think that an IP camera is safe because it is lost in the vast sea of IoT devices, you are sorely mistaken. There are websites like Shodan – basically a search engine for IoT devices. Shodan can reveal IoT devices’ IP addresses and geographic co-ordinates, if you know how to use it. It can even take you straight to the login page of someone’s personal device – like an IP camera. The process is demonstrated below.
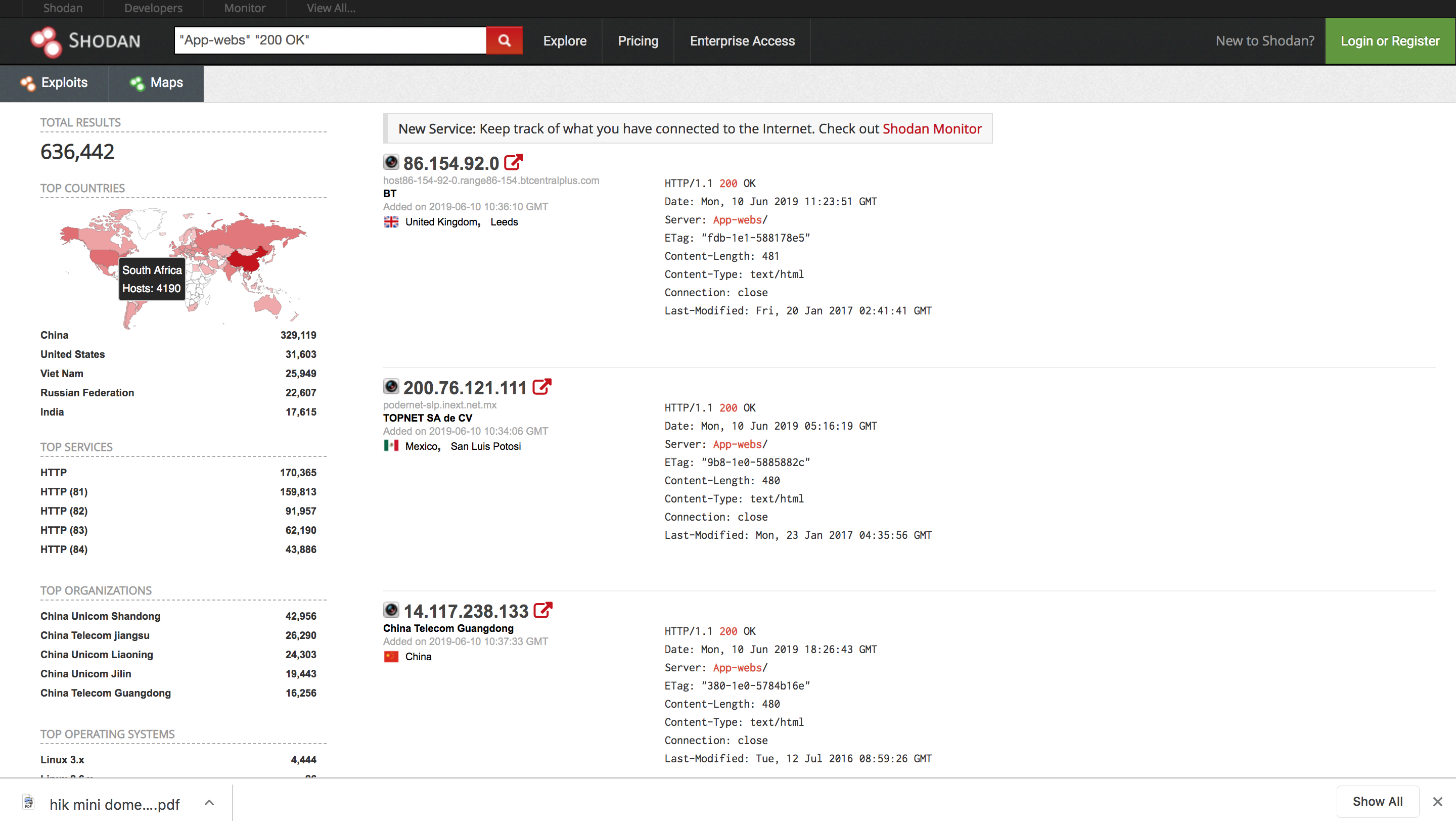 Shodan: The search engine for the Internet-of-Things. As part of their research to map hacked and vulnerable Hikvision cameras, the IPVM engineers used Shodan to search for the company’s cameras globally. This is a screenshot of the search results page (Note: this simply shows where Hikvision cameras are, and not if they are hacked.) The results show more than 600,000 Hikvision devices, with just over 4,000 in South Africa indexed in Shodan. At the top of the results list, is a camera in Leeds in the UK with the IP address 86.154.92.0. Click on the address, and it will show you the device’s exact location — and more.
Shodan: The search engine for the Internet-of-Things. As part of their research to map hacked and vulnerable Hikvision cameras, the IPVM engineers used Shodan to search for the company’s cameras globally. This is a screenshot of the search results page (Note: this simply shows where Hikvision cameras are, and not if they are hacked.) The results show more than 600,000 Hikvision devices, with just over 4,000 in South Africa indexed in Shodan. At the top of the results list, is a camera in Leeds in the UK with the IP address 86.154.92.0. Click on the address, and it will show you the device’s exact location — and more.
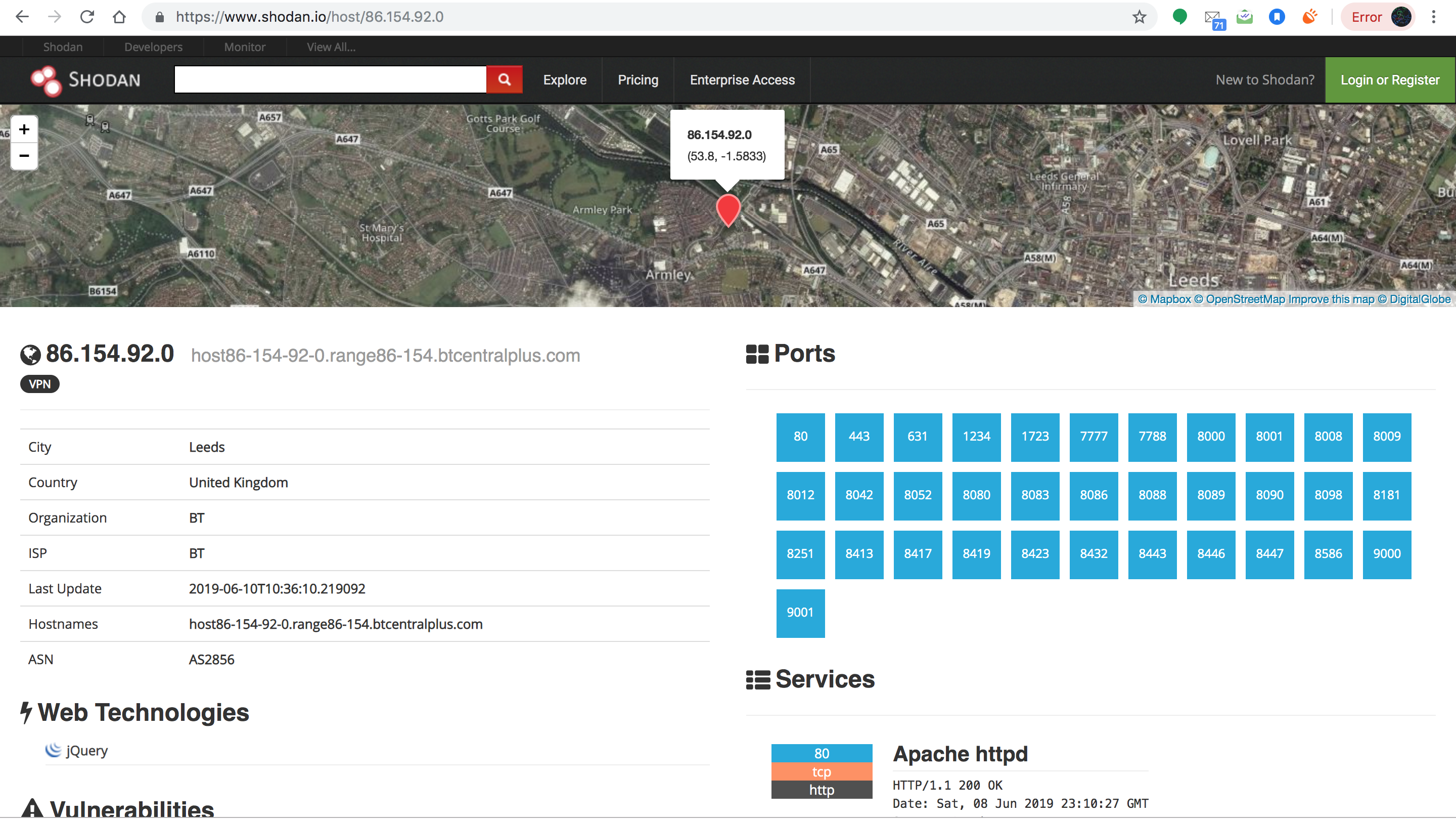 Shodan at work: Clicking on the IP address 86. 154. 92.0 brings up the exact geographic co-ordinates of the camera in Leeds, UK. And plenty of other information.
Shodan at work: Clicking on the IP address 86. 154. 92.0 brings up the exact geographic co-ordinates of the camera in Leeds, UK. And plenty of other information.
 One step closer: Shodan takes you right to the landing page of the specific camera you wish to hack. This is the landing page for the camera in Leeds, UK. Now, the hacking can begin.
One step closer: Shodan takes you right to the landing page of the specific camera you wish to hack. This is the landing page for the camera in Leeds, UK. Now, the hacking can begin.
And this is where the issue of vulnerable surveillance IP cameras starts to affect not only individuals’ personal privacy and safety, but also the stability of the Internet globally. For a hacker, a known IP address is a one-way ticket into a vulnerable IoT device. And a common strategy involves controlling many of these IoT devices and using them collectively to attack a bigger target.
Prominent examples of this type of onslaught, are the Mirai botnet attacks of 2016. Incidentally, IP cameras featured prominently during these attacks.
A botnet attack works like this: Once an IoT device is taken over completely by a hacker, that device is called a “bot”. Several such bots form a botnet (a network of bots), which is then used to launch what’s known as DDoS attack. DDoS stands for Distributed Denial of Service. It’s called a distributed attack because thousands of devices that are distributed all over the world send data to one victim, like a computer server. With so much information coming in, the server is overwhelmed and crashes. It’s basically a digital stoning. With multiple sources attacking, it’s difficult to pinpoint any one culprit and deal with it.
The Mirai malware is thought to have been used in major DDoS attacks. For example, in October 2016 Dyn, the company that provides crucial services upon which prominent sites (like Netflix, Paypal, Twitter, Amazon, and Visa) are dependent, got attacked. The idea was to knock these sites offline. At one stage, most of the US East Coast, as well as data centres in Texas, Washington, and California, were reported to be either knocked off the net, or having network issues.
Back in 2014, the Hikvision cameras-turned-Bitcoin miners were not part of a botnet, but it was an illustration of how easily hackers can get IoT devices to do their bidding. Hikvision responded to the 2014 Bitcoin mining incident by urging customers to update their firmware and set better passwords. But since then, the company has made more concrete changes. Hikvision told Daily Maverick that it was “one of the first companies in the industry to establish a more secure activation process by requiring users to set passwords at the time of first use – rather than the ‘plug and play’ model with a universal password – adding another layer of security.”
But in 2017, an independent researcher, known only by the alias Montecrypto, found a major security flaw in some Hikvision IP cameras – one that would be child’s play to exploit, no matter the strength of the password or obscurity of the username. This time, the US government took notice.
Posting on the web forum IP Cam Talk on 5 March 2017, Montecrypto warned fellow forum members to disconnect their Hikvision cameras from the Internet because he/she had found a vulnerability known as a backdoor.
A backdoor is an entry point into a software system through which an administrator can access that system to maintain it. It allows one to bypass the username and password. Backdoors are often legitimate parts of computer systems built in by a manufacturer. But, manufacturers can also secretly build backdoors into their software to allow them access to their customers’ private systems and data.
Either way, a backdoor leaves a system more vulnerable to hackers.
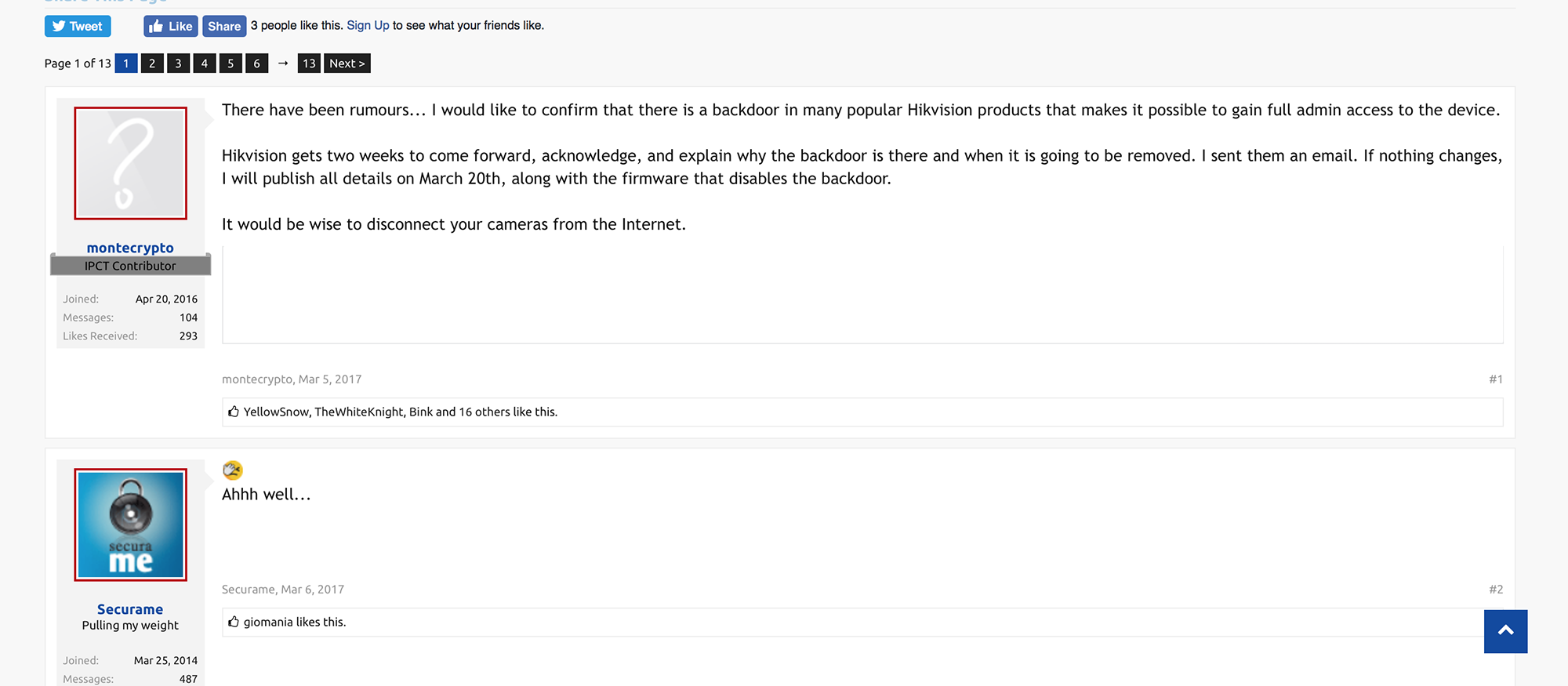 Montecrypto’s post on the IP Cam Talk web forum, an international forum with about 68,000 registered users involved in the IP surveillance industry, including professionals and consumers.
Montecrypto’s post on the IP Cam Talk web forum, an international forum with about 68,000 registered users involved in the IP surveillance industry, including professionals and consumers.
Montecrypto gave Hikvision two weeks to provide a date by which they would have the update ready, and to explain why there was a backdoor in the first place. If they didn’t, he/she would warn the public and release firmware to disable the backdoor.
Hikvision engaged with Montecrypto almost immediately. On 12 and 15 March, they released press statements detailing the threat, with links to new upgrades. Montecrypto delayed the disclosure. By 20 March the US Department of Homeland Security (DHS) had become involved, and on 4 May they issued a warning statement assigning the vulnerability a CVSS score of 10. They credited the discovery to Montecrypto. On the same day, Hikvision posted another warning on their website, declaring that they were working with the DHS on the matter.
But thousands missed the warnings. So, on 12 September 2017, Montecrypto sent out an alert candidly describing the vulnerability as a “severe risk” that is “trivial to exploit”. The researcher said the flaw had been present in the cameras since at least 2014, with “hundreds of thousands” of devices still vulnerable to attack.
IPVM criticised Hikvision’s handling of the situation, stating that, in an attempt to avoid bad press, they did not do enough to let customers know about the vulnerability’s severity. To illustrate how easy it was to hack into affected cameras, the IPVM group set up a test. You can view the demonstration, which lasts just under 90 seconds, here.
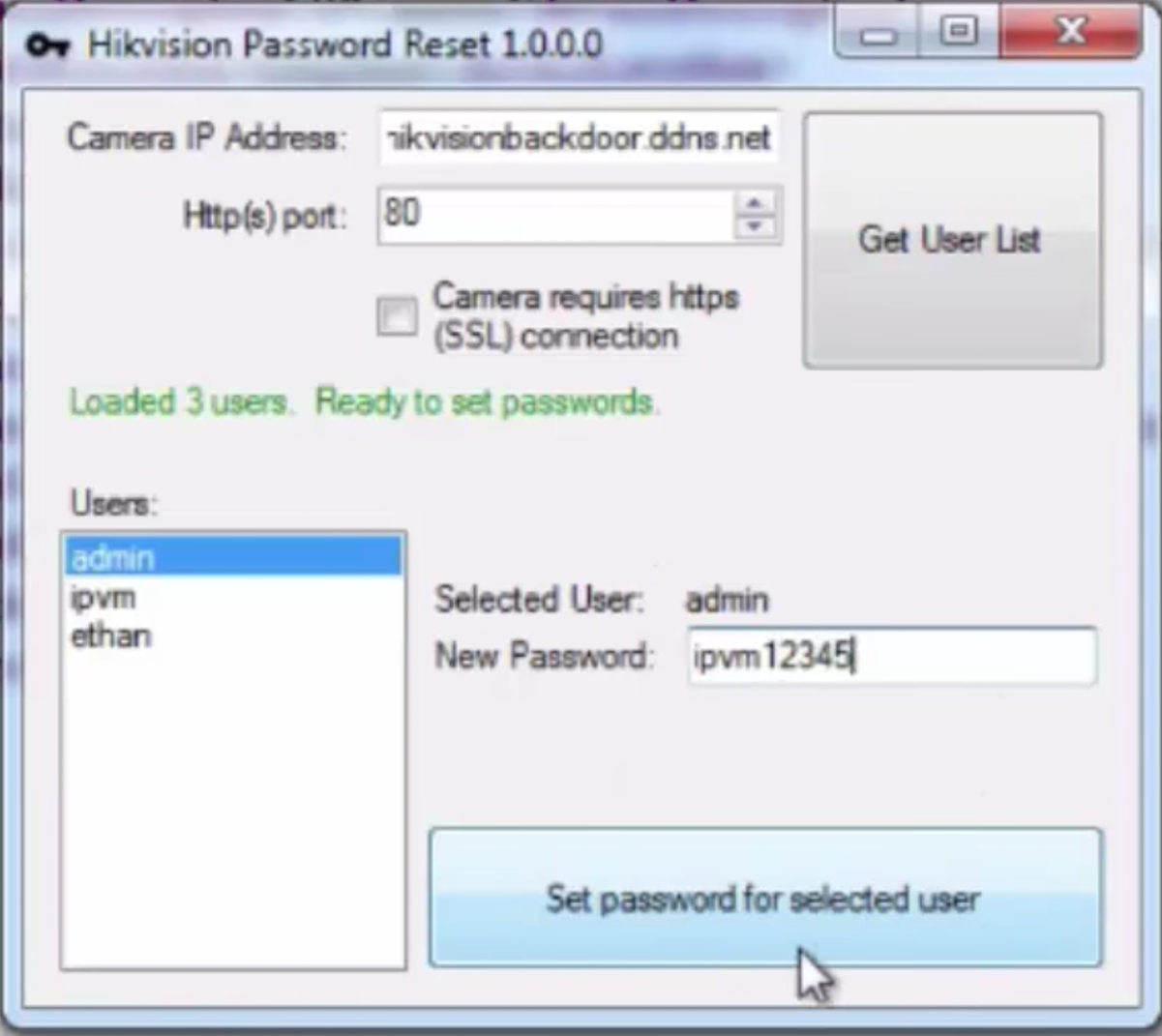 A Hikvision password reset tool used to hack into certain Hikvision IP cameras. The tool was made possible by Montecrypto’s discovery of a back door in various Hikvision models. The IPVM website created this demonstration to show how easy the hack is.
A Hikvision password reset tool used to hack into certain Hikvision IP cameras. The tool was made possible by Montecrypto’s discovery of a back door in various Hikvision models. The IPVM website created this demonstration to show how easy the hack is.
IPVM also set up a map showing thousands of Hikvision cameras throughout the US and Europe that had either been hacked already (about 700 cameras) or were sitting ducks for hackers (about 3,400 cameras). The cameras were monitoring driveways, hotel corridors, laboratories, reception desks, backyards, front doors, kitchens, living rooms, garages, and even a child sleeping in a crib.
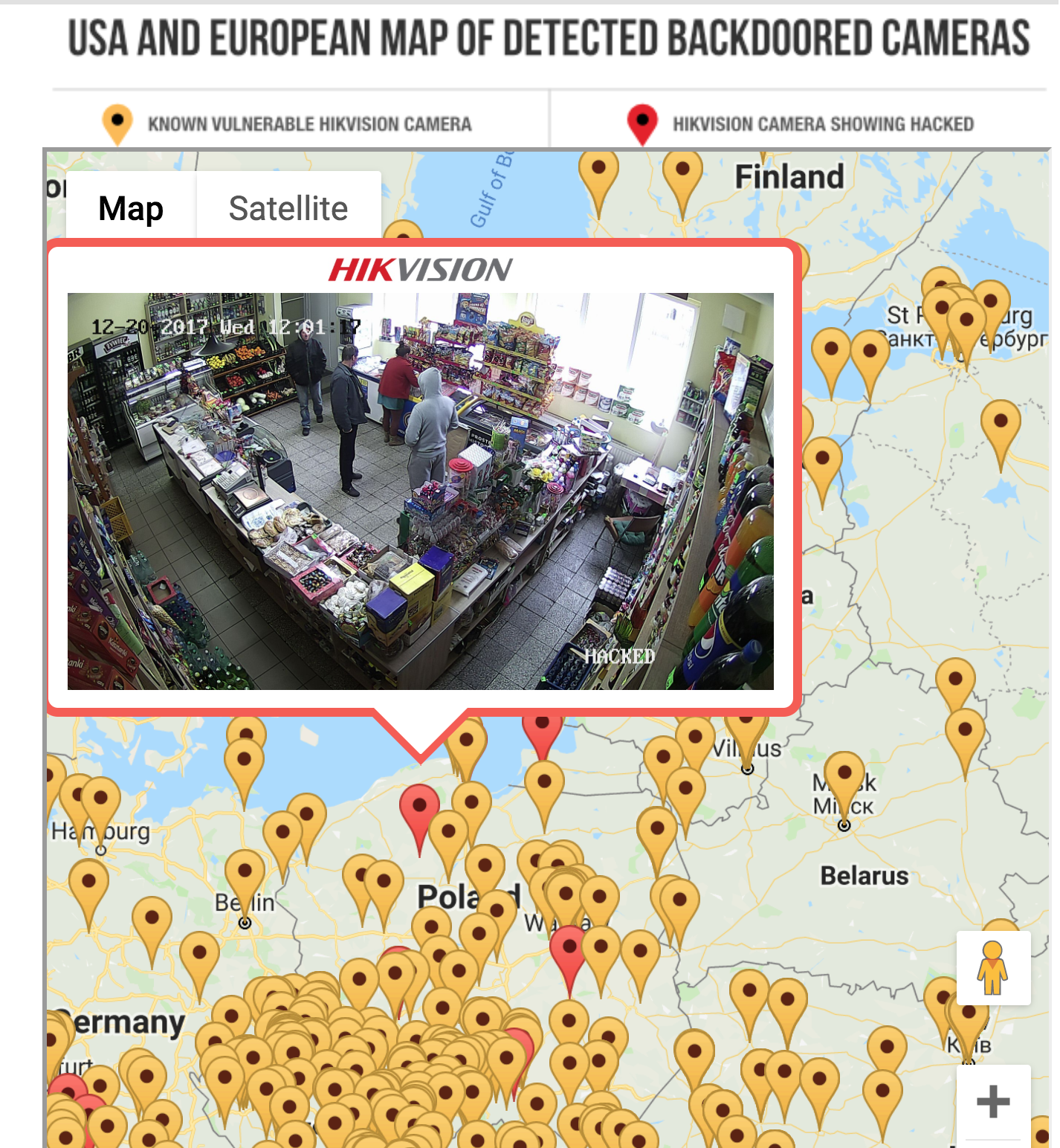 The IPVM group of engineers set up a map of all the Hikvision cameras that remained vulnerable or were already hacked using the backdoor Montecrypto discovered. This picture shows a hacked camera in a small shop in Poland.
The IPVM group of engineers set up a map of all the Hikvision cameras that remained vulnerable or were already hacked using the backdoor Montecrypto discovered. This picture shows a hacked camera in a small shop in Poland.
Neither Hikvision nor the US Department of Homeland Security ever referred to the vulnerability as a “backdoor”, and instead labelled it a privilege-escalating vulnerability. Whether or not the vulnerability was intentionally planted by Hikvision to spy on customers or a careless mistake, remains a topic of debate in IP surveillance circles.
But the issue still contributed to the United States banning its government agencies from using Hikvision equipment through the newly enacted National Defense Authorization Act for the fiscal year 2019. With the US Fearing Chinese espionage, the backdoor only fueled American suspicions.
Asked for comment, a Hikvision corporate spokesperson stated via email: “We’d like to reinforce that there is no evidence anywhere in the world, including South African and the US, to indicate that Hikvision’s products are used for unauthorised collection of information. Hikvision has never conducted, nor will it conduct, any espionage-related activities for any government in the world.”
We asked Hikvision about the allegation that Hikvision does not always disclose the vulnerabilities its research teams discover, and about their slow response times to reports of vulnerabilities in the past.
A company spokesperson stated: “Hikvision manages a world-class enterprise vulnerability management process and is quick to distribute updates and security patches to its customers in collaboration with the US Department of Homeland Security and other industry stakeholders. Hikvision is a CVE Numbering Authority and part of the family of global companies who maintain the CVE vulnerability library. Hikvision is committed to the integrity of its products and industry-leading cybersecurity standards. We work with many globally authoritative third-party organisations in the cybersecurity industry to obtain objective and independent security assessments and authentication. Hikvision products currently meet industry-leading standards including Federal Information Processing Standard (FIPS) 140-2 which was created by the National Institute of Standards and Technology, (NIST), a division of the US Department of Commerce.”
Daily Maverick asked Vumacam why they chose to partner with Hikvision despite its cybersecurity issues. Vumacam spokesperson Ashleigh Parry said they “gave consideration to product performance and integrity, the structure, integrity and sustainability of the surveillance system as a whole, price points and the ability to provide the market with effective access to security” and added that they’re “confident” of the product’s “veracity”, since it was the world’s “leading product”. They also said that the cameras have several safeguards to prevent “hacking and/or any use of feed for any unauthorised activity”, and that the company would take “corrective measures” if their systems were ever compromised. Vumacam said the product continues to meet its robust testing processes.
Asked if they specifically test Hikvision’s firmware for vulnerabilities, Vumacam stated that they “rigorously test any new firmware before deployment in the field. Once in deployment, we have robust internal processes to continuously stress-test and minimise vulnerabilities. With regard to cybersecurity, we go to great lengths to ensure the integrity of our system, protecting ourselves and our clients against any unauthorised access.”
That’s a good thing, because Hikvision’s troubles are not over.
Israeli cybersecurity research group VDOO discovered the latest vulnerability in August 2018. It was an error in the coding of some camera models’ firmware known as a “buffer overflow”. It enabled an attacker to send commands to cameras from a remote location. Again, it required a very low skill level, and with a CVSS score of 9.8, it was critical. At least nine such weaknesses have been discovered in Hikvision products since 2013.
So far, Hikvision’s response time has improved. According to VDOO, Hikvision acted promptly to make available new firmware to solve the problem. As far as could be established, no cameras were hacked.
But whether or not Hikvision’s products can be trusted, is still being debated in surveillance circles. For now, we’ll just have to trust Vumacam’s vision. BM
Heidi Swart is an investigative journalist who reports on surveillance and data privacy issues.
This story was commissioned by the Media Policy and Democracy Project, an initiative of the University of Johannesburg’s department of journalism, film and TV and Unisa’s department of communication science.




 The IPVM group of engineers set up a map of all the Hikvision cameras that remained vulnerable or were already hacked using the backdoor Montecrypto discovered. This picture shows a hacked camera in a small shop in Poland.
The IPVM group of engineers set up a map of all the Hikvision cameras that remained vulnerable or were already hacked using the backdoor Montecrypto discovered. This picture shows a hacked camera in a small shop in Poland.
