I once wrote a novel in which one of the characters imagines a plot for a story in which a nerdy mathematician finds an unknown back door into the cryptography that guards all of the internet, thereby holding the keys to instantaneously reveal everything to anyone. WhatsApp messages, credit card numbers, passwords, access to websites and servers and bank payment systems and blockchains and emails and cellphone conversations. And the databases of the communications of the CIA, FBI, the CCP, the Kremlin and so on.
The sudden unleashing of this mathematical ordinance would basically end the world as we know it, but not revealing it would crush our hapless mathematician under its ethical weight.
Is this a realistic possibility?
The mathematics underlying the secrets of digital communications has been around publicly since the 1970s, when a group of researchers developed a technique called asymmetric cryptography, an extremely clever exploitation of a set of well known, but unusual sets of mathematical whatnots called the one-way functions.
There is little doubt that various state actors and individual miscreants have committed resources to try to hack and crack these encryption tools; the incentives are, well, beyond imagining. Anyone holding this power would have access to untold wealth and power and influence, depending on their tastes and predilections.
But we must assume that no one has broken the lock (although one never knows, given the dark arts and uber-tech of the National Security Agency). The computational effort to achieve that task is actually not that complicated to work out. Given the current state of things, it would take, well, a long, long, long time using all the computer power on Earth to brute-force an attack (100 trillion years for most standard encryption used today, according to Google’s Bard).
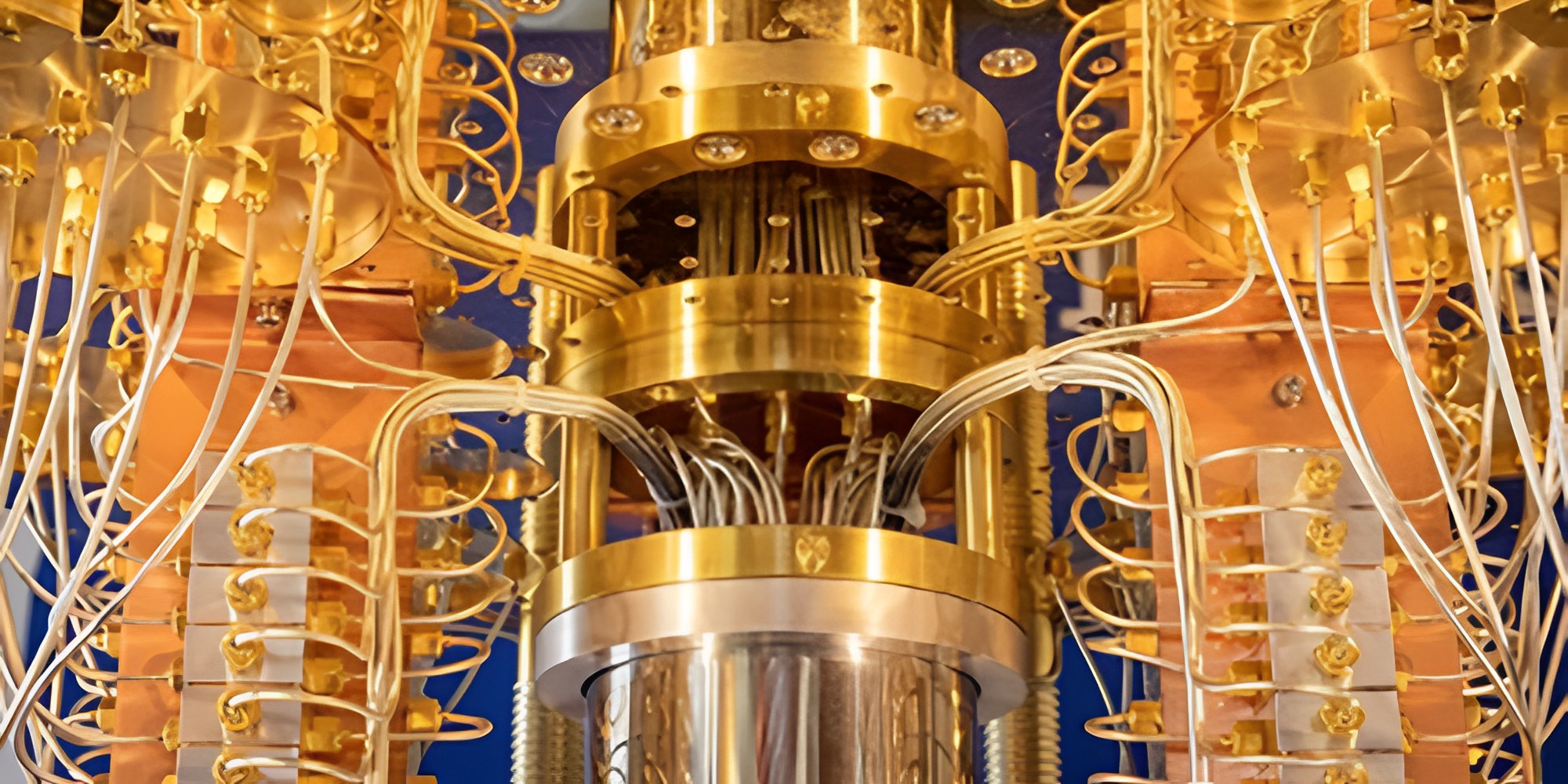
Quantum computing
This brings us to another technology that has been buzzing quietly in the background for some decades, that of quantum computing. The promise of this technology is well known — it will (if ever properly harnessed) unleash computing speeds so far in excess of today’s as to be beyond our ability to really understand what it would portend. Certainly fast enough to eat current encryption algorithms for breakfast.
I am not going to try to explain how it works, because its details are deep into the world of particle physics, way beyond my pay grade, but here is the principle.
A bit can be a one or a zero expressed as an on/off electric current somewhere in the tiny wires among billions (yes, billions) of transistors on a chip in your laptop. All of computing starts there — ones and zeros, on or off. But a quantum bit, called a qubit, can be in an infinite number of states, each with a different probability of being “true” at any given moment. Which will allow computation speeds many magnitudes greater than the standard binary bit-based computers.
So what? one may reasonably ask. Well, it’s complicated, because it will not make a quantum computer faster than your laptop on every task. But for some other problems, it will blaze. Like the factoring of numbers into their largest component prime numbers (like 21=7*3).
Factoring into prime numbers is the central core of current encryption algorithms guarding the internet.
The alarmist narrative gets a little irrational here. It says that the internet cannot be fully trusted because when quantum computing gets here it will all go pear-shaped and we will not be able to secure anything, and our civilisation will instantly implode.
Two problems
There are two problems here. The first is the question of when. When is this moment going to arrive? When do we wake up to the headlines: “The internet is over! Security cracked in two seconds by Chinese secret service using quantum computing!”?
It turns out that the big players in quantum computing, like Google, IBM, Microsoft, Amazon, Intel, D-Wave Systems, Rigetti Computing and numerous other public or hidden state actors have been moving two steps forwards and one step backwards for quite a while, at least as far back as the 1980s when famed physicists Richard Feynman and David Deutsch first proposed it.
A number of practical problems have intruded along the way, like the devilish problem of “noise” or errors in quantum measurement. This is a well-known problem that plagues the quantum world, but not our everyday macro world.
There is also the problem of temperature — most approaches require the machines to operate at near absolute zero, which is expensive to do and so unlikely to be on your desk at home any time soon.
While some top academics like computer scientist Leonard Adleman at USC, mathematician Peter Shor at MIT and physicist David Awschalom at the University of Chicago believe that the noise problem will be solved within 10 years, others, like physicist David Mermin at Cornell University, believe it’s a “pipe dream”.
Cryptographers and crackers
But more importantly, there is the long history of wars between cryptographers and crackers, dating way back to ancient days. It’s a war between those who invent secret-keeping mechanisms and those who look for ways to circumvent them, each one bettering the other for some period of time.
That leads to this rather obvious statement: as soon as quantum computing gets close to cracking standard encryption, so will cryptographers already have developed quantum-resistant algorithms, although this is unlikely to be a smooth and trouble-free process.
For instance, in August 2022, a team of researchers from the University of Luxembourg and the University of New South Wales announced that they had broken the Supersingular Isogeny Key Encapsulation (Sike) algorithm, a post-quantum encryption algorithm that was being considered for standardisation by the National Institute of Standards and Technology.
Perhaps naively, I have full confidence that the cryptographers will be able to build a non-crackable post-quantum encryption algorithm. The stakes are simply too high to imagine any other outcome. A rare moment of optimism tells me that it is not time to worry.
Yet. DM
Steven Boykey Sidley is a professor of practice at JBS, University of Johannesburg.